Configure SSO with Azure AD Authorization
If you use Azure Active Directory (Microsoft Entra ID, hereinafter referred to as Azure AD) to manage your enterprise accounts, you can select Azure AD as the authorization server configuration and enable Single Sign-On (SSO) in InHand Cloud Service. You also need to configure OpenID Connect (OIDC) in Azure AD. This article provides an example of user SSO with Azure AD and InHand Cloud Service to help you understand the end-to-end configuration process of SSO for connection authorization between Enterprise Identity Provider (IdP) and InHand Cloud Service.
Pre-requisites
● An InHand Cloud Service system administrator account.
● Already have an Azure tenant with an administrator account (with global administrative privileges granted). You need to use the administrator account to perform the operations in Azure AD in this example. For information on how to create users and authorize users in Azure AD, see the Azure AD Portal.
You have a corporate employee user (test_sso) in Azure AD, and you want the corporate employee user (test_sso) to be able to SSO directly to the InHand Cloud Service by logging in to Azure AD.
Step 1: Get the callback address in InHand Cloud Service
1. Log in to InHand Cloud Service using your system administrator account.
2. Select System Settings >> Azure AD in the navigation bar.
3. Click Add.
4. Copy the Web Redirect URIs in the pop-up window. This address will be used for the configuration of the application in Azure AD.
Step 2: Create an application in Azure
1. Sign in to the Azure portal using an administrator account.
2. go to the Home page and click Microsoft Entra ID.
3. In the left menu bar, click Application Registrations.
4. Click New Registration and fill in the following information:
a. A customized application name, for example, InCloud_Beta.
b. Select the type of tenant that needs to use the application.
c. Fill in the redirection URI copied in InHand Cloud Service.
d. Click Register to complete the creation of the new application.
Step 3: Configure SSO information in InHand Cloud Service
1. Configure the ID information of Azure AD in InHand Cloud Service:
a. Application (client) ID: Corresponds to the Application (Client) ID on the Application Overview page in Azure AD.
b. Directory (tenant) ID: corresponds to the Directory (Tenant) ID of the Application Overview page in Azure AD.
2. In the Azure portal, click Certificates and Secrets in the left menu bar.
3. On the Client Secrets page, click New Client Secret, fill in the description and expiration date, and then click Add; then copy the generated value ;
4. Fill the value into the Azure AD information in InHand Cloud Service and submit.
Note: The client secret generated in Azure AD has an expiration date, after the secret expires, the SSO function cannot be used, please create a new client secret in advance to replace it.
Step 4: Create users and authorize applications in Azure AD
1. On the Application Overview page of the Azure portal, click Go to Enterprise Applications. 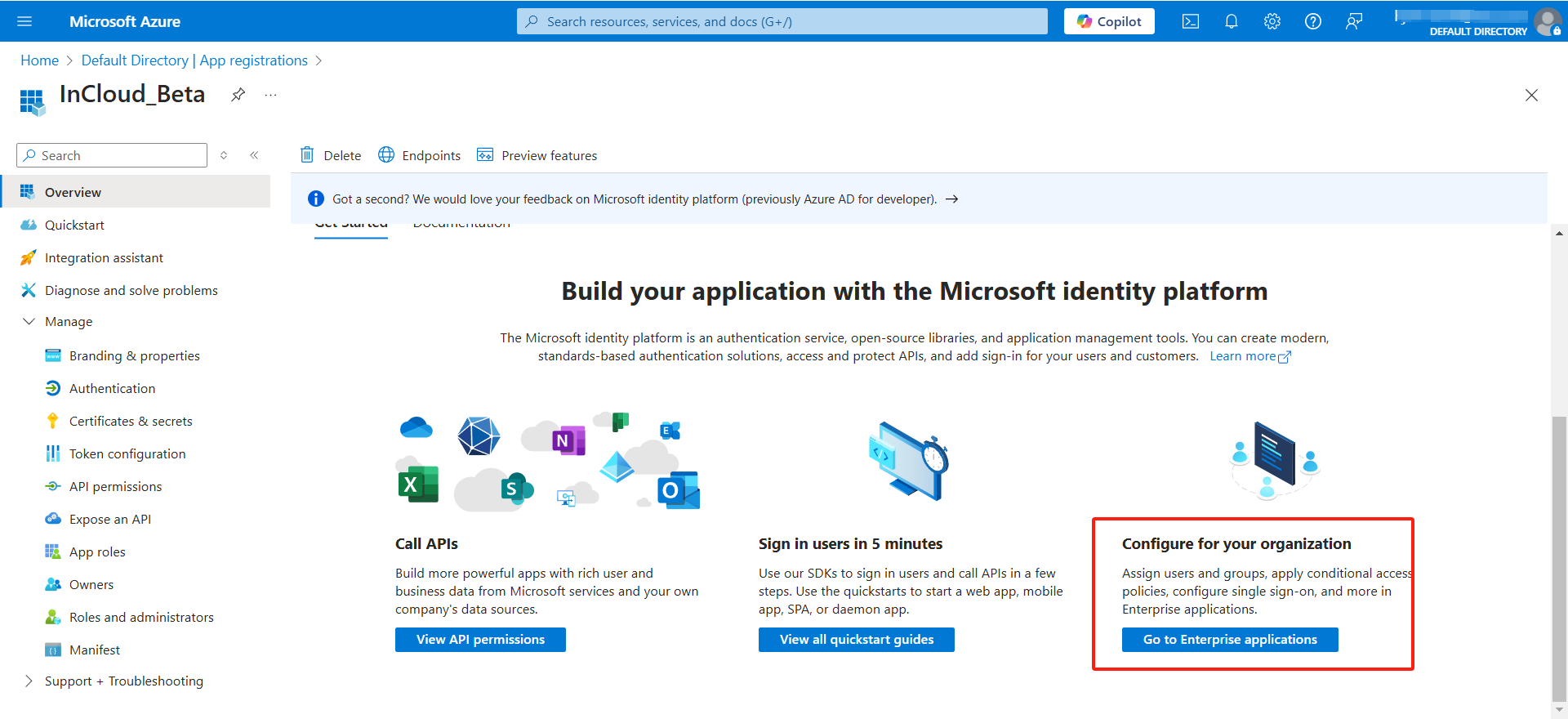
2. In the left menu bar, click Users and Groups.
3. Click Add User/group and select the user/group you want to authorize, such as test_sso@inhand.com.
4. Click Assign to complete the application authorization for the user.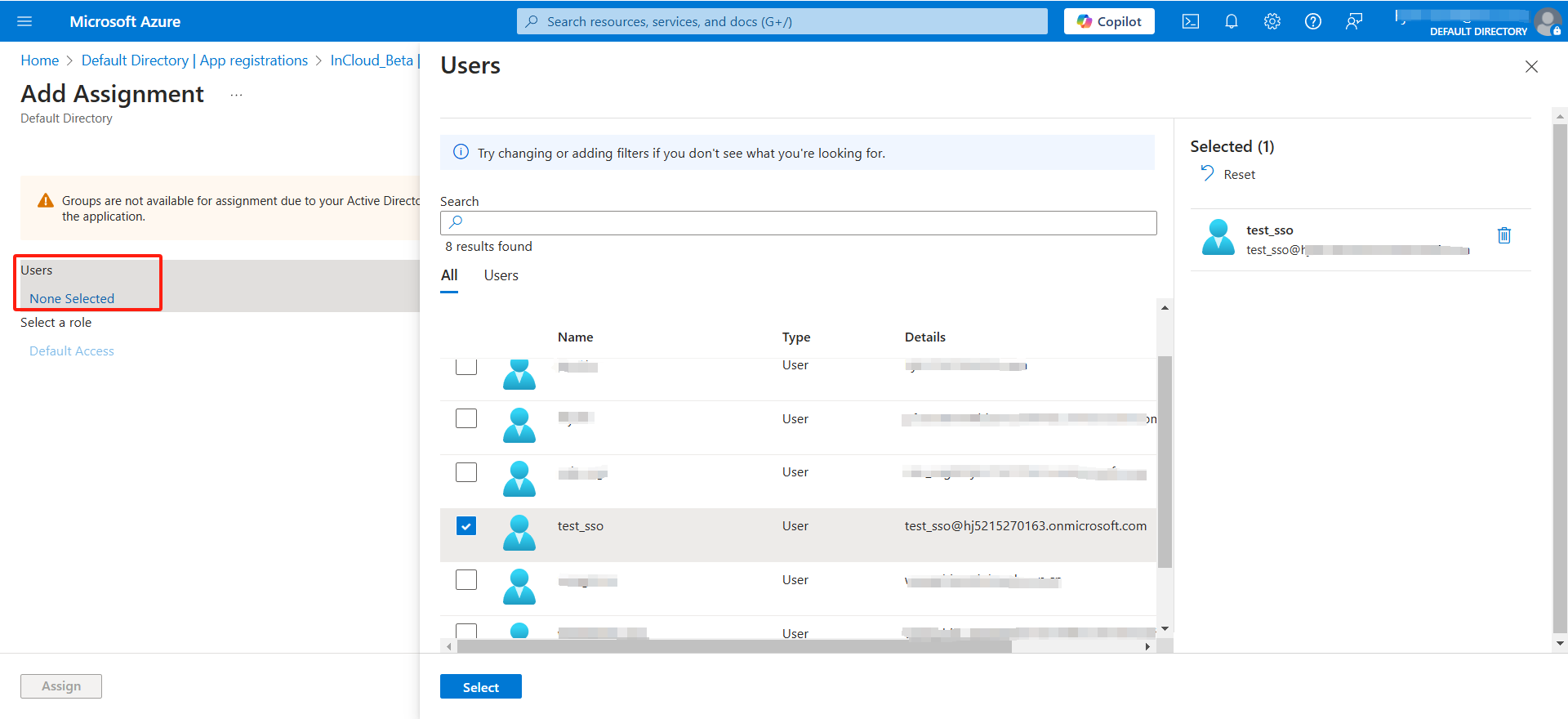
Step 5: Create sub-users in InHand Cloud Service
1. Go to the Users page of InHand Cloud Service.
2. Click Add at the top right of the user list.
3. Fill in the pop-up window with the account that is authorized in the Azure portal and submit it, e.g., test_sso@inhand.com.
Verification Result
1. Go to the InHand Cloud Service login page and click Azure Login.
2. Enter the email address you need to sign in, such as test_sso@inhand.com, and click Sign In.
3. Select the same account as the one you entered in the previous step, e.g,test_sso@inhand.com. if not, you can click Add to use another account.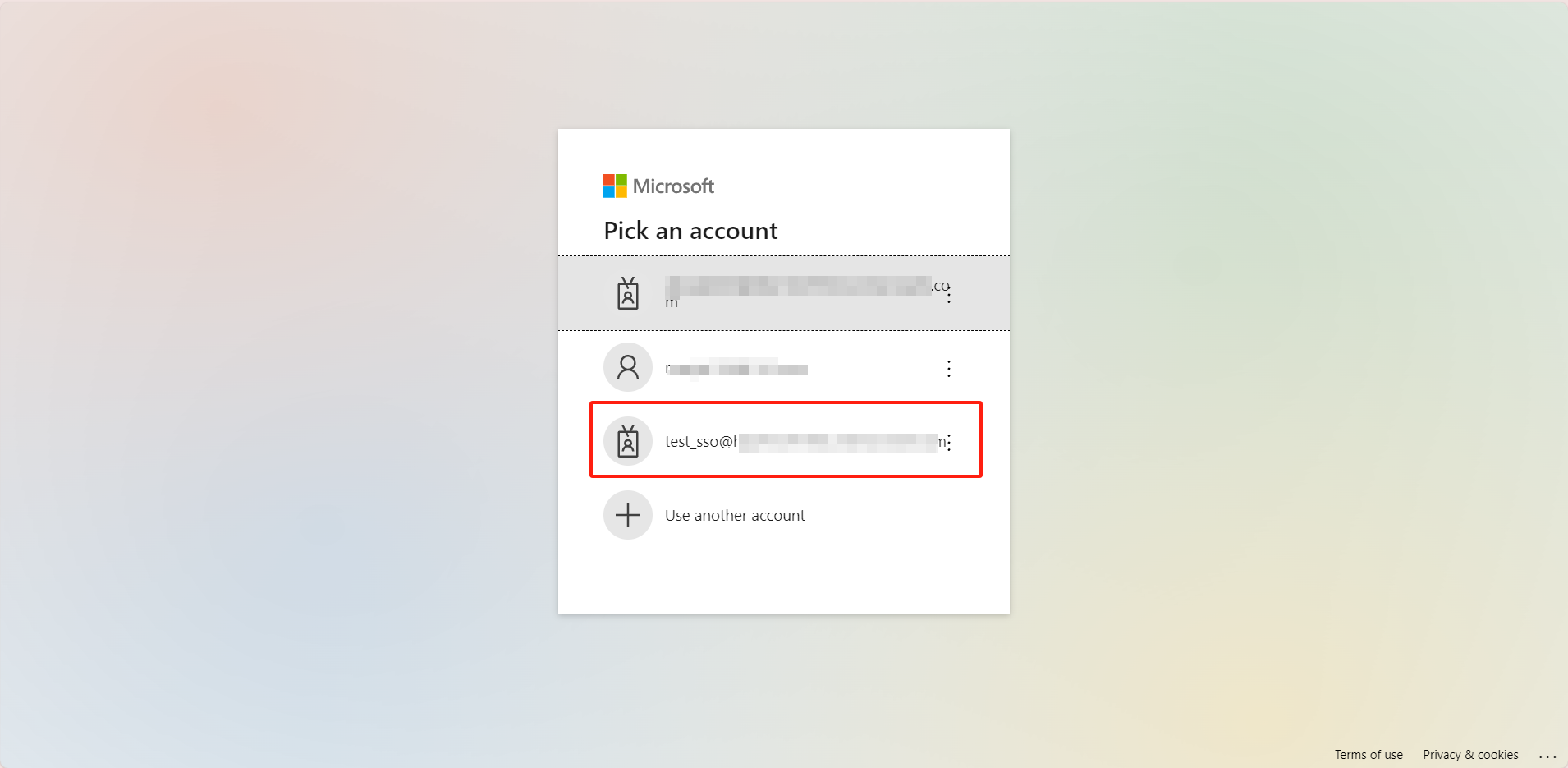
4. Enter the password for this account in the Azure portal and sign in.
FAQ
1.After the configuration is complete, users are still unable to sign in with their Azure accounts
Please confirm the following information:
● The Azure AD information configured in InHand Cloud Service is correct;
● The Azure client password is within the validity period;
● The accounts for Azure and InHand Cloud Service are the same;
● The password for login is the password for the Azure portal.
2.You cannot log in with the Azure account after using it for a period of time
Please confirm the following information:
● The Azure client password is within the validity period;
● The account still has permissions for this application in the Azure portal.
3.Can I use the account password to sign in after configuring Azure AD sign-in?
After you configure Azure AD, you can still sign in using the password you configured in the platform.
Related Articles
Device Manager User Manual
1.About the Platform Device Manager ("DM") is an Internet of Things (IoT) device management cloud platform of the "new generation" independently developed and operated by InHand. With visual user interfaces (UIs) and easy-to-use processes, it allows ...DeviceLive User Manual
About the Platform DeviceLive platform is designed for the industrial IoT field to quickly build intelligent edge networks paired with InHand edge intelligent hardware. It has four major capabilities: device management, remote monitoring, edge ...InCloud Manager User Manual
About the platform The InCloud Manager is a cloud-based network management platform. Integrating InHand edge routers and AP, it helps enterprises build a modern network environment and quickly realize digital retail and office. InCloud Manager ...AI Assistant User Guide
This document introduces the capabilities and usage guidelines of the InCloud Manager AI Assistant. Note: This feature is currently in public beta. Stay tuned for the official release. Overview The InCloud Manager AI Assistant is an intelligent ...InConnect User Manual
1. About InConnect InHand Connect Service cloud platform (hereinafter referred to as InConnect) is a "one-stop" networking service provided for enterprise customers. It features user-friendly interface and simple operations. InConnect can be used ...